The Kremlin-backed hackers who focused SolarWinds clients in a provide chain assault have been caught conducting a malicious electronic mail marketing campaign that delivered malware-laced hyperlinks to 150 authorities companies, analysis establishments and different organizations within the US and 23 different international locations, Microsoft mentioned.
The hackers, belonging to Russia’s Foreign Intelligence Service, first managed to compromise an account belonging to USAID, a US authorities company that administers civilian international assist and improvement help. With management of the company’s account for on-line advertising and marketing firm Constant Contact, the hackers had the power to ship emails that appeared to make use of addresses identified to belong to the US company.
Nobelium goes native
“From there, the actor was able to distribute phishing emails that looked authentic but included a link that, when clicked, inserted a malicious file used to distribute a backdoor we call NativeZone,” Microsoft Vice President of Customer Security and Trust Tom Burt wrote in a post revealed on Thursday night. “This backdoor could enable a wide range of activities from stealing data to infecting other computers on a network.”
The marketing campaign was carried out by a gaggle that Microsoft calls Nobelium and is often known as APT29, Cozy Bear, and the Dukes. Security agency Kaspersky has said that malware belonging to the group dates again to 2008, whereas Symantec has said the hackers have been concentrating on governments and diplomatic organizations since at the very least 2010. There’s extra concerning the off-kilter and old-school coding traits of this group here.
Last December, Nobelium’s notoriety reached a brand new excessive with the invention the group was behind the devastating breach of SolarWinds, an Austin, Texas, maker of community administration instruments. After totally compromising SolarWinds’ software program improvement and distribution system, the hackers distributed malicious updates to about 18,000 clients who used the device, which was known as Orion. The hackers then used the updates to compromise 9 federal companies and about 100 private-sector corporations, White House officers have mentioned.
Security agency FireEye mentioned that along with the USAID content material, the hacking group used quite a lot of different lures, together with diplomatic notes and invites from embassies. It went on to say that the marketing campaign’s concentrating on of governments, assume tanks and associated organizations has been a conventional focus for operations carried out by the Foreign Intelligence Service, which is named the SVR.
“Though the SolarWinds activity was remarkable for its stealth and discipline, loud, broad spearphishing operations were once the calling card of SVR operators who often carried out noisy phishing campaigns,” John Hultquist, Vice President of Analysis at FireEye-owned Mandiant Threat Intelligence, mentioned in an electronic mail. “Those operations were often effective, gaining access to major government offices among other targets. And while the spear phishing emails were quickly identified, we expect that any post-compromise actions by these actors would be highly skilled and stealthy.”
Blast from the previous
On Tuesday, Nobelium blasted 3,000 totally different addresses with emails that presupposed to ship a particular alert from USAID regarding new paperwork Former President Trump had revealed about election Fraud. One of the emails appeared like this:
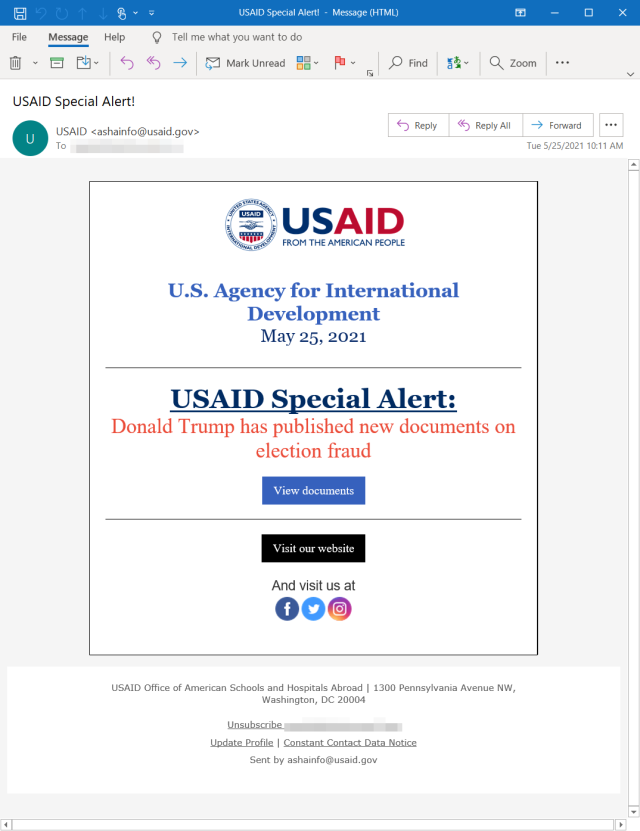
Microsoft
People who clicked on the hyperlink had been first delivered to the official Constant Contact service, however shortly after that they had been redirected to a file hosted on servers belonging to Nobelium, Microsoft mentioned. Once targets had been redirected, JavaScript prompted customer gadgets to routinely obtain a sort of archive file often known as an ISO picture.
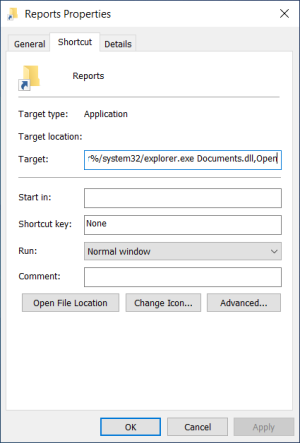
As the picture under exhibits, the ISO picture contained a PDF file, a LNK file named Reports, and a DLL file named paperwork, which by default was hidden.
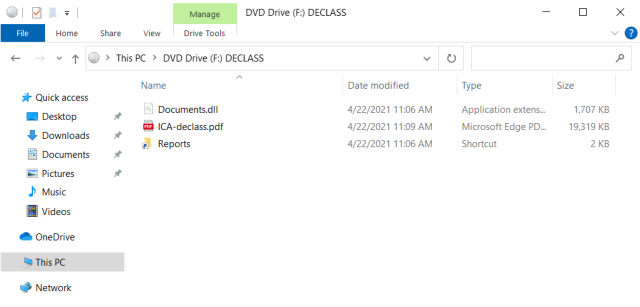
Microsoft
When a goal clicked on the Reports file, it opened the PDF as a decoy and within the background executed the DLL file. The DLL, in flip, put in the NativeZone backdoor. A separate post revealed by the Microsoft Threat Intelligence Center, or MSTIC, mentioned the backdoor allowed Nobelium to attain persistent entry to compromised machines so the group might “conduct action-on objectives, such as lateral movement, data exfiltration, and delivery of additional malware.”
Tuesday’s assault was simply the newest wave of what MSTIC mentioned was a widespread malicious spam marketing campaign that began in late January. Since then, the marketing campaign has developed in a collection of iterations which have demonstrated “significant experimentation.”
When Microsoft first noticed the marketing campaign, it was internet hosting the ISO on Firebase, a Google-owned cloud platform for cell and Web apps. During this early iteration, Microsoft mentioned, the ISO picture contained no malicious payload, main firm researchers to conclude the aim was to “record attributes of those who accessed the URL.” In a later section, the marketing campaign despatched emails that contained an HTML file. When opened, JavaScript wrote an ISO picture to disc and inspired the goal to open it.
The circulation of this latter assault section appeared like this:
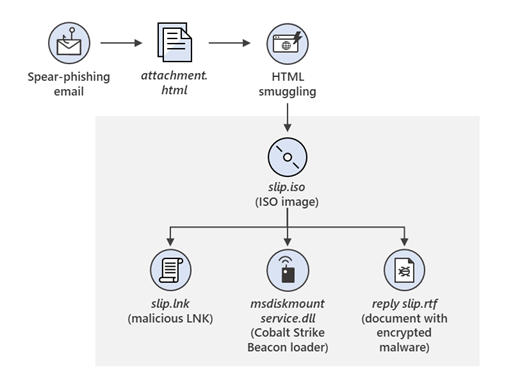
Microsoft
iOS zero-day
Nobelium continued to experiment with a number of variations. In one wave, no ISO payload was delivered in any respect. Instead, a Nobelium-controlled net server profiled the goal machine. In the occasion the focused machine was an iPhone or iPad, a server delivered what was then a zero-day exploit for CVE-2021-1879, an iOS vulnerability that allowed hackers to ship a common cross-site scripting assault. Apple patched the zero-day in late March.
Thursday night’s MSTIC publish continued:
Experimentation continued by means of a lot of the marketing campaign however started to escalate in April 2021. During the waves in April, the actor deserted the usage of Firebase, and not tracked customers utilizing a devoted URL. Their strategies shifted to encode the ISO inside the HTML doc and have that answerable for storing goal host particulars on a distant server through the usage of the api.ipify.org service. The actor typically employed checks for particular inside Active Directory domains that might terminate execution of the malicious course of if it recognized an unintended atmosphere.
In May 2021, the actor modified strategies as soon as extra by sustaining the HTML and ISO mixture, however dropped a customized .NET first-stage implant, detected as TrojanDownloader:MSIL/BoomBox, that reported host-based reconnaissance knowledge to, and downloaded further payloads from, the Dropbox cloud storage platform.
On May 25, the NOBELIUM marketing campaign escalated considerably. Using the official mass mailing service Constant Contact, NOBELIUM tried to focus on round 3,000 particular person accounts throughout greater than 150 organizations. Due to the high-volume marketing campaign, automated techniques blocked a lot of the emails and marked them as spam. However, automated techniques may need efficiently delivered a few of the earlier emails to recipients.
Security agency Volexity, in the meantime, revealed its own post on Thursday that gives extra particulars nonetheless. Among them: the Documents.DLL file checked goal machines for the presence of safety sandboxes and digital machines as proven right here:
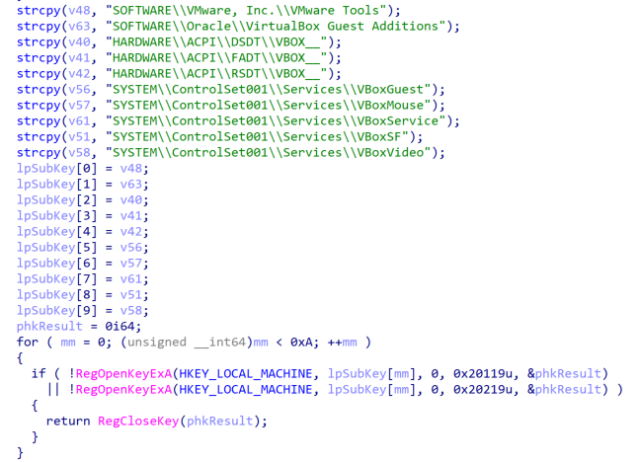
Volexity
Both MSTC and Volexity offered a number of indicators of compromise that organizations can use to find out in the event that they had been focused within the marketing campaign. MSTC went on to warn that this week’s escalation isn’t possible the final we’ll see of Nobelium or its ongoing electronic mail marketing campaign.
“Microsoft security researchers assess that the Nobelium’s spear-phishing operations are recurring and have increased in frequency and scope,” the MSTC publish concluded. “It is anticipated that additional activity may be carried out by the group using an evolving set of tactics.”
Post up to date at 8:51 California time so as to add particulars from FireEye.