
DarkSide—the ransomware group that disrupted gasoline distribution throughout a large swath of the US this week—has gone darkish, leaving it unclear if the group is ceasing, suspending, or altering its operations or is just orchestrating an exit rip-off.
On Thursday, all eight of the darkish websites DarkSide used to speak with the general public went down, and so they stay down as of publication time. Overnight, a submit attributed to DarkSide claimed, with out offering any proof, that the group’s web site and content material distribution infrastructure had been seized by legislation enforcement, together with the cryptocurrency it had obtained from victims.
The canine ate our funds
“At the moment, these servers cannot be accessed via SSH, and the hosting panels have been blocked,” the submit acknowledged, in accordance with a translation of the Russian-language submit published Friday by safety agency Intel471. “The hosting support service doesn’t provide any information except ‘at the request of law enforcement authorities.’ In addition, a couple of hours after the seizure, funds from the payment server (belonging to us and our clients) were withdrawn to an unknown account.”
The submit went on to say that DarkSide would distribute a decryptor freed from cost to all victims who’ve but to pay a ransom. So far, there aren’t any stories of the group delivering on that promise.
If true, the seizures would symbolize an enormous coup for legislation enforcement. According to newly released figures from cryptocurrency monitoring agency Chainalysis, DarkSide netted at the least $60 million in its first seven months, with $46 million of it coming within the first three months of this yr.
Identifying a Tor hidden service would even be an enormous rating, because it seemingly would imply that both the group made a serious configuration error in setting the service up or legislation enforcement is aware of of a severe vulnerability in the way in which the darkish net works. (Intel471 analysts say that a few of DarkSide’s infrastructure is public-facing—which means the common Internet—so malware can hook up with it.)
But thus far, there’s no proof to publicly corroborate these extraordinary claims. Typically, when legislation enforcement from the US and Western European nations seize a web site, they submit a discover on the positioning’s entrance web page that discloses the seizure. Below is an instance of what individuals noticed after making an attempt to go to the positioning for the Netwalker group after the positioning was taken down:
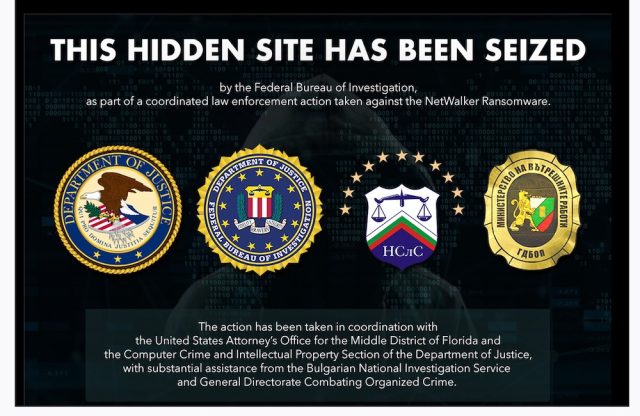
So far, not one of the DarkSide websites show such a discover. Instead, most of them outing or present clean screens.
What’s much more uncertain is the declare that the group’s appreciable cryptocurrency holdings have been taken. People who’re skilled in utilizing digital foreign money know to not retailer it in “hot wallets,” that are digital vaults linked to the Internet. Because sizzling wallets comprise the personal keys wanted to switch funds to new accounts, they’re weak to hacks and the forms of seizures claimed within the submit.
For legislation enforcement to confiscate the digital foreign money, DarkSide operators seemingly would have needed to retailer it in a sizzling pockets, and the foreign money change utilized by DarkSide would have needed to cooperate with the legislation enforcement company or been hacked.
I very a lot doubt {that a} ransomware group retains its earnings in a sizzling pockets on a cryptocurrency change that may cooperate with the legislation enforcement. They go to shady exchanges solely when they should launder the cash. Even then, blocking could be extra plausible than switch.
— Vess (@VessOnSafety) May 14, 2021
It’s additionally possible that shut monitoring by a corporation like Chainalysis recognized wallets that obtained funds from DarkSide, and legislation enforcement subsequently confiscated the holdings. Indeed, Elliptic, a separate blockchain analytics firm, reported discovering a Bitcoin wallet used by DarkSide to obtain funds from its victims. On Thursday, Elliptic reported, it was emptied of $5 million.
At the second, it is not identified if that switch was initiated by the FBI or one other legislation enforcement group, or by DarkSide itself. Either approach, Elliptic stated the pockets—which since early March had obtained 57 funds from 21 completely different wallets—offered essential clues for investigators to comply with.
“What we find is that 18% of the Bitcoin was sent to a small group of exchanges,” Elliptic Co-founder and Chief Scientist Tom Robinson wrote. “This information will provide law enforcement with critical leads to identify the perpetrators of these attacks.”
Nonsense, hype, and noise
DarkSide’s submit got here as a distinguished prison underground discussion board referred to as XSS introduced that it was banning all ransomware actions, a serious about-face from the previous. The website was beforehand a big useful resource for the ransomware teams REvil, Babuk, DarkSide, LockBit, and Nefilim to recruit associates, who use the malware to contaminate victims and in change share a reduce of the income generated. Just a few hours later, all DarkSide posts made to XSS had come down.
In a Friday morning post, safety agency Flashpoint wrote:
According to the administrator of XSS, the choice is partially primarily based on ideological variations between the discussion board and ransomware operators. Furthermore, the media consideration from high-profile incidents has resulted in a “critical mass of nonsense, hype, and noise.” The XSS assertion presents some causes for its resolution, significantly that ransomware collectives and their accompanying assaults are producing “too much PR” and heightening the geopolitical and legislation enforcement dangers to a “hazard[ous] level.”
The admin of XSS additionally claimed that when “Peskov [the Press Secretary for the President of Russia, Vladimir Putin] is forced to make excuses in front of our overseas ‘friends’—this is a bit too much.” They hyperlinked an article on the Russian News web site Kommersant entitled “Russia has nothing to do with hacking attacks on a pipeline in the United States” as the idea for these claims.
Within hours, two different underground boards—Exploit and Raid Forums—had additionally banned ransomware-related posts, according to pictures circulating on Twitter.
REvil, in the meantime, stated it was banning using its software program in opposition to well being care, academic, and governmental organizations, The Record reported.
Ransomware at a crossroads
The strikes by XSS and REvil pose a serious short-term disruption of the ransomware ecosystem since they take away a key recruiting instrument and income. Long-term results are much less clear.
“In the long run, it’s hard to believe the ransomware ecosystem will completely fade out, given that operators are financially motivated and the schemes employed have been effective,” Intel471 analysts stated in an electronic mail. They stated it was extra seemingly that ransomware teams will “go private,” which means they may now not publicly recruit associates on public boards or will unwind their present operations and rebrand below a brand new title.
Ransomware teams may additionally alter their present apply of encrypting knowledge so it is unusable by the sufferer whereas additionally downloading the info and threatening to make it public. This double-extortion methodology goals to extend the strain on victims to pay. The Babuk ransomware group lately began phasing out its use of malware that encrypts knowledge whereas sustaining its weblog that names and shames victims and publishes their knowledge.
“This approach allows the ransomware operators to reap the benefits of a blackmail extortion event without having to deal with the public fallout of disrupting the business continuity of a hospital or critical infrastructure,” the Intel471 analysts wrote within the electronic mail.
For now, the one bits of proof that DarkSide’s infrastructure and cryptocurrency have been seized are the phrases of admitted criminals, hardly sufficient to think about affirmation.
“I could be wrong, but I suspect this is simply an exit scam,” Brett Callow, a risk analyst with safety agency Emsisoft, instructed Ars. “DarkSide get to sail off into the sunset—or, more likely rebrand—without needing to share the ill-gotten gains with their partners in crime.”