

When you go to an HTTPS-protected web site, your browser would not trade information with the webserver till it has ensured that the positioning’s digital certificates is legitimate. That prevents hackers with the flexibility to observe or modify information passing between you and the positioning from acquiring authentication cookies or executing malicious code on the visiting system.
But what would occur if a man-in-the-middle attacker might confuse the browser into by chance connecting to an e-mail server or FTP server that makes use of a certificates that is appropriate with the one utilized by the web site?
The perils of talking HTTPS to an e-mail server
Because the area identify of the web site matches the area identify within the e-mail or FTP server certificates, the browser will, in lots of instances, set up a Transport Layer Security reference to certainly one of these servers slightly than the web site the person meant to go to.
Because the browser is speaking in HTTPS and the e-mail or FTP server is utilizing SMTP, SFTP, or one other protocol, the likelihood exists that issues would possibly go horribly flawed—a decrypted authentication cookie could possibly be despatched to the attacker, for example, or an attacker might execute malicious code on the visiting machine.
The state of affairs is not as farfetched as some individuals would possibly suppose. New analysis, in reality, discovered that roughly 14.4 million webservers use a website identify that is appropriate with the cryptographic credential of both an e-mail or FTP server belonging to the identical group. Of these websites, about 114,000 are thought of exploitable as a result of the e-mail or FTP server makes use of software program that is recognized to be susceptible to such assaults.
Such assaults are potential due to the failure of TLS to guard the integrity of the TCP connection itself slightly than the integrity of simply the server talking HTTP, SMTP, or one other Internet language. Man-in-the-middle attackers can exploit this weak spot to redirect TLS site visitors from the meant server and protocol to a different, substitute endpoint and protocol.
“The basic principle is that an attacker can redirect traffic intended for one service to another, because TLS does not protect the IP address or port number,” Marcus Brinkmann, a researcher at Ruhr University Bochum in Germany, informed me. “In the past, people have considered attacks where the MitM attacker redirects a browser to a different web server, but we are considering the case where the attacker redirects the browser from the webserver to a different application server such as FTP or email.”
Cracks within the cornerstone
Typically abbreviated as TLS, Transport Layer Security makes use of robust encryption to show that an finish person is related to an genuine server belonging to a selected service (comparable to Google or Bank of America) and never an impostor masquerading as that service. TLS additionally encrypts information because it travels between an finish person and a server to make sure that individuals who can monitor the connection cannot learn or tamper with the contents. With hundreds of thousands of servers counting on it, TLS is a cornerstone of on-line safety.
In a research paper revealed on Wednesday, Brinkmann and 7 different researchers investigated the feasibility of utilizing what they name cross-protocol assaults to bypass TLS protections. The approach includes an MitM attacker redirecting cross-origin HTTP requests to servers that talk over SMTP, IMAP, POP3, or FTP, or one other communication protocol.
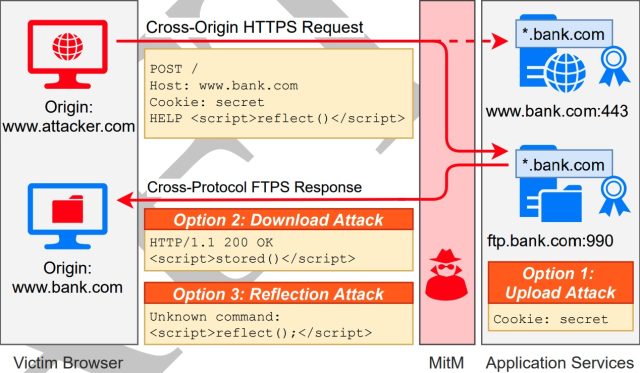
The principal elements of the assault are (1) the consumer utility utilized by the focused finish person, denoted as C; (2) the server the goal meant to go to, denoted as Sint; and (3) the substitute server, a machine that connects utilizing SMTP, FTP, or one other protocol that is completely different from the one serverint makes use of however with the identical area listed in its TLS certificates.
The researchers recognized three assault strategies that MitM adversaries might use to compromise the secure shopping of a goal on this state of affairs. They are:
Upload Attack. For this assault, we assume the attacker has some capability to add information to Ssub and retrieve it later. In an add assault, the attacker tries to retailer elements of the HTTP request of the browser (particularly the Cookie header) on Ssub. This would possibly, for instance, happen if the server interprets the request as a file add or if the server is logging incoming requests verbosely. On a profitable assault, the attacker can then retrieve the content material on the server independently of the connection from C to Ssub and retrieve the HTTPS session cookie.
Download Attack—Stored XSS. For this assault, we assume the attacker has some capability to arrange saved information on Ssub and obtain it. In a obtain assault, the attacker exploits benign protocol options to “download” beforehand saved (and particularly crafted) information from Ssub to C. This is just like a saved XSS vulnerability. However, as a result of a protocol completely different from HTTP is used, even subtle protection mechanisms in opposition to XSS, just like the Content-Security-Policy
(CSP), may be circumvented. Very probably, Ssub won’t ship any CSP by itself, and enormous elements of the response are beneath the management of the attacker.Reflection Attack—Reflected XSS. In a mirrored image assault, the attacker tries to trick the server Ssub into reflecting elements of C’s request in its response to C. If profitable, the attacker sends malicious JavaScript inside the request that will get mirrored by Ssub. The consumer will then parse the reply from the server, which in flip can result in the execution of JavaScript within the context of the focused internet server.
The MitM adversary cannot decrypt the TLS site visitors, however there are nonetheless different issues the adversary can do. Forcing the goal’s browser to connect with an e-mail or FTP server as a substitute of the meant webserver, for example, would possibly trigger the browser to put in writing an authentication cookie to the FTP server. Or it might allow cross-site scripting assaults that trigger the browser to obtain and execute malicious JavaScript hosted on the FTP or e-mail server.
Enforcing ALPN and SNI protections
To forestall cross-protocol assaults, the researchers proposed stricter enforcement of two present protections. The first is named application layer protocol negotiation, a TLS extension that permits an utility layer comparable to a browser to barter what protocol must be utilized in a safe connection. ALPN, because it’s normally abbreviated, is used to ascertain connections utilizing the better-performing HTTP/2 protocol with out further spherical journeys.
By strictly imposing ALPN because it’s outlined within the formal standard, connections created by browsers or different app layers that ship the extension should not susceptible to cross-protocol assaults.
Similarly, use of a separate TLS extension referred to as server name indication can shield in opposition to cross-hostname assaults if it is configured to terminate the connection when no matching host is discovered. “This can protect against cross-protocol attacks where the intended and substitute server have different hostnames, but also against some same-protocol attacks such as HTTPS virtual host confusion or context confusion attacks,” the researchers wrote.
The researchers are calling their cross-protocol assaults ALPACA, brief for “application layer protocols allowing cross-protocol attacks.” At the second, ALPACA would not pose a significant risk to most individuals. But the danger posed might improve as new assaults and vulnerabilities are found or TLS is used to guard further communications channels.
“Overall, the attack is very situational and targets individual users,” Brinkmann stated. “So, the individual risk for users is probably not very high. But over time, more and more services and protocols are protected with TLS, and more opportunities for new attacks that follow the same pattern arise. We think it’s timely and important to mitigate these issues at the standardization level before it becomes a larger problem.”