

Malicious hackers have been exploiting a vulnerability in totally up to date variations of macOS that allowed them to take screenshots on contaminated Macs with out having to get permission from victims first.
The zero-day was exploited by XCSSET, a bit of malware discovered by security firm Trend Micro final August. XCSSET used what on the time have been two zero-days to contaminate Mac builders with malware that stole browser cookies and recordsdata; injected backdoors into web sites; stole data from Skype, Telegram, and different put in apps; took screenshots; and encrypted recordsdata and confirmed a ransom observe.
A 3rd zero-day
Infections got here within the type of malicious initiatives that the attacker wrote for Xcode, a software that Apple makes out there totally free to builders writing apps for macOS or different Apple OSes. As quickly as one of many XCSSET initiatives was opened and constructed, TrendMicro mentioned, the malicious code would run on the builders’ Macs. An Xcode mission is a repository for all of the recordsdata, assets, and knowledge wanted to construct an app.
In March, researchers from SentinelOne found a new a trojanized code library within the wild that additionally put in the XCSSET surveillance malware on developer Macs.
On Monday, researchers with Jamf, a safety supplier for Apple enterprise customers, mentioned that XCSSET has been exploiting a zero-day that had gone undetected till lately. The vulnerability resided within the Transparency Consent and Control framework, which requires specific person permission earlier than an put in app can receive system permissions to entry the onerous drive, microphone, digicam, and different privacy- and security-sensitive assets.
XCSSET had been exploiting the vulnerability so it may bypass TCC protections and take screenshots with out requiring person permission. Apple mounted CVE-2021-30713 (because the vulnerability is tracked) on Monday with the discharge of macOS 11.4.
The vulnerability was the results of a logic error that allowed XCSSET to cover contained in the listing of an put in app that already had permission to take screenshots. The exploit allowed the malware to inherit the screenshot permissions, in addition to different privileges managed by TCC.
Piggybacking off mum or dad apps
“Some developers design applications with smaller applications placed within them,” Jamf researcher Jaron Bradley mentioned in an interview. “This isn’t unheard of. But a bug appears to have existed in the operating system logic when it comes to how the TCC permissions are handled in such a situation.”
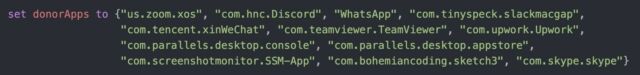
To find apps that XCSSET may piggyback off of, the malware checked for display screen seize permissions from a listing of put in purposes.
“As expected, the list of application IDs that are targeted are all applications that users regularly grant the screen sharing permission to as part of its normal operation,” Bradley wrote in a post. “The malware then uses the following mdfind command—the command-line-based version of Spotlight—to check if the appID’s are installed on the victim’s device.”
Jamf
The put up defined how the movement of the AppleScript accountable for the exploit labored:
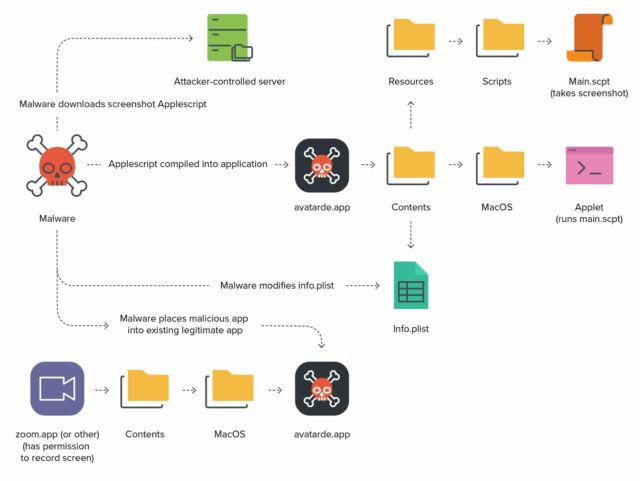
- The XCSSET AppleScript screenshot module is downloaded from the malware writer’s command and management (C2) server (to the ~/Library/Caches/GameKit folder).
- Using the osacompile command, the screenshot module is transformed to an AppleScript-based software known as avatarde.app. When any AppleScript is compiled on this method, an executable known as “applet” is positioned within the newly created software bundle’s /Contents/MacOS/ listing and the script that the applet will execute will be positioned at /Contents/Resources/Scripts/major.scpt.
- The newly created Info.plist is then modified by the plutil binary, altering the choice setting LSUIElement to true. This permits the applying to be run as a background course of, concealing its presence from the person.
- A clean icon is then downloaded and utilized to the applying.
- Lastly, the newly created software is positioned throughout the already current donor software utilizing the next code:
For instance, if the digital assembly software zoom.us.app is discovered on the system, the malware will place itself like so:
/Applications/zoom.us.app/Contents/MacOS/avatarde.app
If the sufferer pc is working macOS 11 or larger, it is going to then signal the avatarde software with an ad-hoc signature, or one that’s signed by the pc itself.
Once all recordsdata are in place, the customized software will piggyback off of the mum or dad software, which within the instance above is Zoom. This signifies that the malicious software can take screenshots or report the display screen without having specific consent from the person. It inherits these TCC permissions outright from the Zoom mum or dad app. This represents a substantial privateness concern for end-users.
During Jamf’s testing, it was decided that this vulnerability shouldn’t be restricted to display screen recording permissions both. Multiple completely different permissions which have already been supplied to the donor software will be transferred to the maliciously created app.
Jamf
Now that Apple has mounted the vulnerability, TCC works the way in which Apple supposed, with a dialog message that prompts customers to both open the system preferences to permit the app or to easily click on the deny button displayed by the popup.
XCSSET isn’t more likely to infect Macs until it has run a malicious Xcode mission. That means individuals are unlikely to be contaminated until they’re builders who’ve used one of many initiatives. The Jamf put up supplies indicators of a compromise listing that individuals can use to find out in the event that they’ve been contaminated.